Yesterday was patchday for Magento. On this occasion, I would like to provide insights into how we at integer_net handle scheduled security updates. Thanks to this process, we could update the shops for all 20 active projects within less than 24 hours.

Our plannable and structured approach
- Utilizing Adobe's Release Schedule: We leverage the structured release schedule provided by Adobe, in which security patches are released every two months. This predictability allows us to plan our patch deployment process well in advance, ensuring smooth execution without any last-minute surprises.
- Roles and Responsibilities: One month prior to patchday, we assign roles to team members. There is a patchday coordinator and a developer responsible for risk assessment. Both with a substitute in case of unforeseen circumstances. This ensures clear accountability and streamlines the patch deployment process.
- Transparent Communication: We proactively inform customers about upcoming patches, ensuring transparency and building trust. Also, they can plan acceptance testing on their side in advance. We create tickets for each project, keeping everyone involved informed about the status every step of the way. They are linked to a main patchday ticket so that our patchday coordinator always has full overview.
- Robust QA Plan: We establish a QA plan for each project, clearly outlining who is responsible for testing. We use Qase for test case management. For patchdays there is a test run template in each project that contains only high priority tests, so that we can quickly assess if critical functionality is still working.
Additionally, based on the developer’s risk assessment of the changed code, we determine which features are affected and should be tested closely. - Priority: A security update has the highest priority. It SHOULD be deployed to production as soon as possible. Any other releases, or an update of the Magento versions, MUST NOT block the security patch. There are no exceptions, even if the regular release is already on staging!
For CRITICAL patches, we have an emergency process and the rule that all shops MUST be patched within 24 hours max (our record is at around 6 hours). In doubt, that means, we do not wait for customer acceptance tests for their own good.
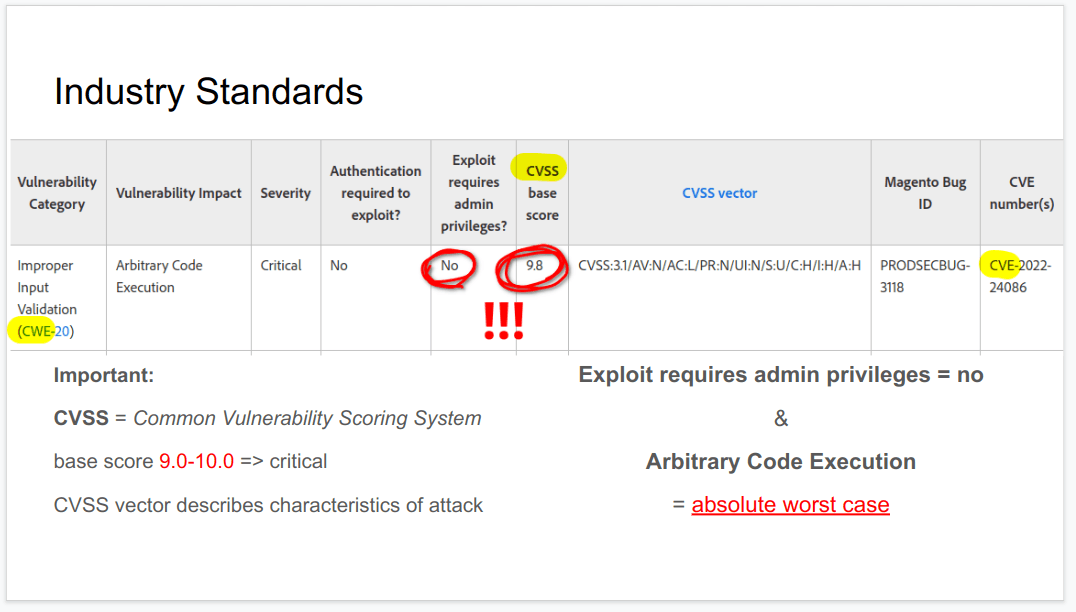
What’s a CRITICAL patch?
We use the Common Vulnerability Scoring System (CVSS) to determine how critical the security issue is. A security patch related to a vulnerability with CVSS score of 9.0-10.0 is considered CRITICAL.
CVSS scores for Magento security updates can be found at https://helpx.adobe.com/security/security-bulletin.html#magento
As soon as they are available, the patchday coordinator checks if the “critical emergency patch” process must be initiated. In that case, the whole team only has one priority together: patch all shops ASAP.
Conclusion
At integer_net, we understand that security is not just a one-time effort but an ongoing commitment. That's why we continuously monitor and update our security processes to stay ahead of emerging threats and vulnerabilities. With us, you can rest assured that your Magento store is in safe hands, allowing you to focus on what you do best – running and growing your business.
This is all possible thanks to the predictable, standardized security release process from Adobe.
Image credits: Alan O’Rourke (CC-BY 2.0)